Authorization
SlashDB users can be granted permissions to:
Personal Information
The lowest level of authorization grants access to the API, GUI and basic user information.
Info
A user who has login credentials and has not been granted any extra permissions is able to access only their own user configuration and modify only some of those settings: password, API key, full name, and email.
For example, user john makes a GET request for his user information using the API. The request is authenticated by passing his API key:
curl -i "https//localhost/userdef/john.json" \
-H "apikey: 3pewxln1nnrm3lcz04vuj0rmisveya6q"
or by viewing it in the GUI by clicking on his user initial in upper right corner and selecting Settings from the dropdown menu:
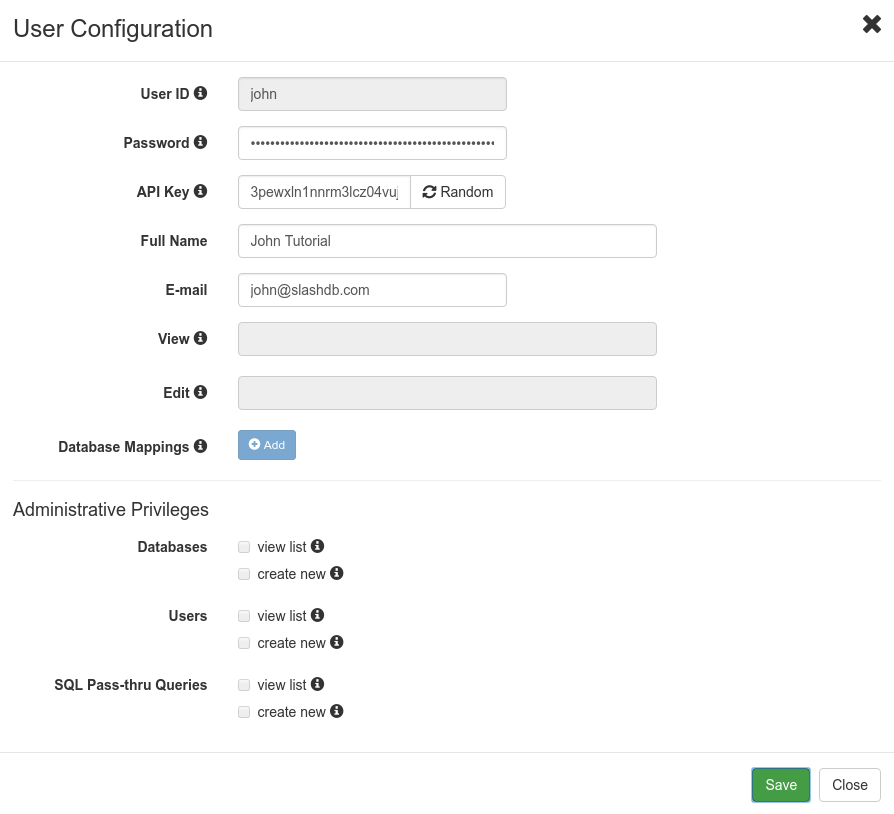
This brings up a screen with the user's information:
Data
A user's access to data is controlled by their Database Mappings. A database mapping associates a user account with a database account that has previously been configured on a database.
Mappings are configured on the User Configuration screen.
Info
The benefits of mapping SlashDB user accounts to database accounts include:
- ability to leverage security mechanisms which are built into databases (
GRANT,GROUPS,ROLESetc.) - you can create SlashDB accounts that have different effective privileges on database objects (e.g. only
SELECT) - avoiding complicated permissions control logic in the application
Data Discovery
Authenticated SlashDB users may only access databases that they have mappings for. Only mapped databases will be listed in the database list at the /db endpoint.
Example
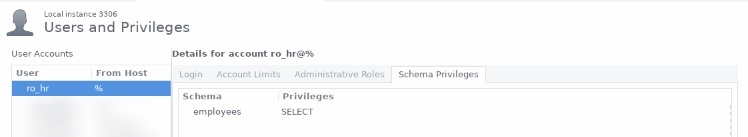
Configure SlashDB user mike to have read permissions on a database named hr by mapping his account to the database account ro_hr which is granted only SELECT privileges in the database configuration.
First, configure the database account using its administrative console; e.g. for a MySQL database hr with an account named ro_hr:
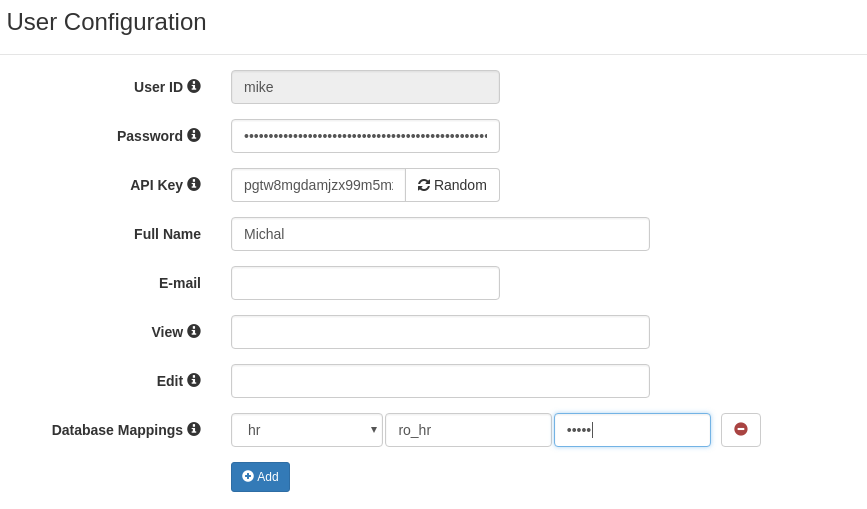
Next, in SlashDB, create a database mapping to the hr database (assumes hr database has been added to SlashDB) for the SlashDB user mike:
Now you can retrieve data from the hr database using mike's account:
curl -i 'http://localhost/db/hr/departments.json' -H 'apikey: pgtw8mgdamjzx99m5mxf8sfeipwkdw0u'
HTTP/1.1 200 OK
But attempts to update data fail:
curl -i -X POST 'http://localhost/db/hr/departments.json' \
-H 'apikey: pgtw8mgdamjzx99m5mxf8sfeipwkdw0u' \
-d '{"dept_name": "New Dept", "dept_no": "d020"}'
HTTP/1.1 404 Not Found
Warning: (_mysql_exceptions.OperationalError) (1142, "INSERT command denied to user 'ro_hr'@'pc140.home' for table 'departments'")
{"http_code": 404, "description": "(_mysql_exceptions.OperationalError) (1142, \"INSERT command denied to user 'ro_hr'@'pc140.home' for table 'departments'\")"}
SQL Pass-thru
Two levels of authorization have to be configured to execute a query:
- The SlashDB user must be allowed to execute the query. The user can be given execute privileges from the Query Configuration screen.
- A database mapping must be created for the SlashDB user to a database account that can execute the query.
SlashDB Configuration
Important
By default, modifying SlashDB configuration items is restricted to the admin user.
You can grant administrative privileges to other user accounts to view and modify these configurations too. This is particularly useful if you need to have one or more power users with some control over the system.
SlashDB contains several configuration sections:
- create new database connections
- view/edit database connections
- connect/disconnect databases
- allow users to view/edit a given user's configuration
- allow users to view lists of databases, users, SQL Pass-thru queries or database credentials
- allow users to create new databases, users, SQL Pass-thru queries, or database credentials
- allow users to view/edit a given query's configuration
- allow users to execute a given query
- allow users to view/edit database credentials
- allow users to assign database credentials to other users when creating database mappings